Why You Should Swap Passwords for Passphrases
Oct 22, 2025
The Hacker News
The advice didn't change for decades: use complex passwords with uppercase, lowercase, numbers, and symbols. The idea is to make passwords harder for hackers to crack via brute force methods. But more recent guidance shows our focus should be on password length, rather than complexity. Length is the more important security factor, and passphrases are the simplest way to get your users to create (and remember!) longer passwords.
The math that matters#
When attackers steal password hashes from a breach, they brute-force by hashing millions of guesses per second until something matches. The time this takes depends on one thing: how many possible combinations exist.
A traditional 8-character "complex" password (P@ssw0rd!) offers roughly 218 trillion combinations. Sounds impressive until you realize modern GPU setups can test those combinations in months, not years. Increase that to 16 characters using only lowercase letters, and you're looking at 26^16 combinations, billions of times harder to crack.
This is effective entropy: the actual randomness an attacker must work through. Three or four random common words strung together ("carpet-static-pretzel-invoke"![]() deliver far more entropy than cramming symbols into short strings. And users can actually remember them.
deliver far more entropy than cramming symbols into short strings. And users can actually remember them.
https://thehackernews.com/2025/10/why-you-should-swap-passwords-for.html?_m=3n%2e009a%2e3805%2eqb0ao44uux%2e2ue2
usonian
(23,977 posts)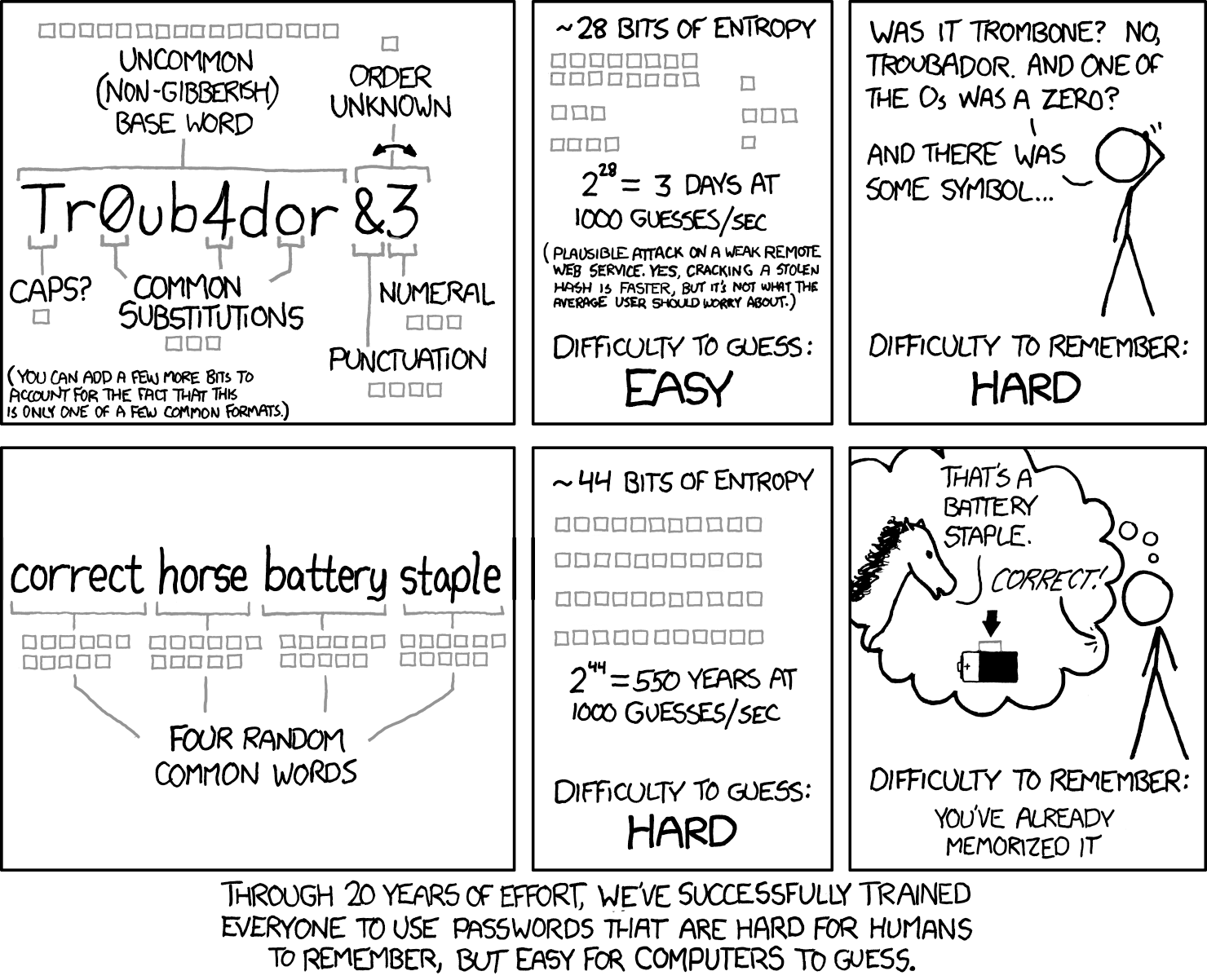
Here are some sites that will generate passphrases for you (I don't know about their security/privacy policy. Please check first)
https://correcthorse.pw/
https://xkpass.com/
On the other hand .....

This is how some bitcoin wallets get stolen. The (very) brute force way.
------------------------------
And way technical:
https://www.explainxkcd.com/wiki/index.php/936:_Password_Strength
But very seriously. When I was department sysadmin, I was checking one of the workstations and didn't know the password. I looked at a picture on the wall, of some musical or opera and there was the password. Nailed it in 10 seconds.
Passages
(3,986 posts)usonian
(23,977 posts)One clever trick (not my invention) was to hack the "passwd" command, so that when people entered new or changed passwords, they were checked against dictionaries on the way IN, when they were unencrypted. This was lightning fast compared to cracking them (with my white hat on) after they were entered and encrypted by the system.
And the usual culprits turned up in the latter. 12345, and a bunch of department-related and dumb/naughty stuff.
I very strongly recommend a password manager app. I use Samurai Safe. (1)
That way, I can create really obscure passwords for various sites (I won't share how I create them, though most password managers will offer to do it for. you) and gladly forget them, asking the app for the password when needed.
You can also save a PDF (optionally encrypted) of your passwords, in case you are incapacitated. Put the printout in a lockbox, or give someone that you trust the password.
(1) https://samarama.net/
For ios and macos.
Free always.
PoindexterOglethorpe
(28,484 posts)So far it's 118 passwords long.
I really hate the sites that require a new password periodically.
Passages
(3,986 posts)It can be annoying.
usonian
(23,977 posts)Password manager apps are designed to do this, and some synch across devices.
Password managers are also free or cheap.
I manage the app's "vault" file (and/or copies) and trust nobody else to manage them (you saw what happened when Amazon AWS faceplanted)
Safe Computing!
PoindexterOglethorpe
(28,484 posts)But I bet my 118 are not close to a record, even for a relatively casual internet user as myself.
And I doubt anyone will ever hack this computer to find my password file. Meanwhile, the big companies screw up password management all the time.
usonian
(23,977 posts)Malware can rummage through your files.
My ex had a printer problem. She googled (avoid google like the plague) HP printer support, and some creep faked it, and got high rank via SEO. Had her install remote desktop to diagnose (it's malware) and so on.
She eventually cleaned up the mess.
I encrypt sensitive files. Just now, I went through all my phone photos that I transferred to the computer. License, credit cards .... all dragged to a doc folder that I am encrypting right now.
Not entirely paranoid.
"just enough?"
I tell everyone: "Ask me before doing anything on the computer." ![]()
Your computer is connected to the internet. Your lockbox isn't. YET
PoindexterOglethorpe
(28,484 posts)I do voice, and rarely, text on my phone. I don't do the promiscuous on-line stuff most people do on their phones. Oddly enough, I simply don't get things suddenly taking over my computer. Safe Computing is a lot like Safe Sex.
I have something called SpamArrest on my computer which means 99% of spam goes straight to that folder. And I've long known not to click on anything unsolicited.
I'm also good at researching, don't just always go for the first result. I'm also inclined to do things like take my computer back to the store where I bought it and have them help out.
I am sorry your wife had the printer problem.
And if you don't google, how do you find anything? I've never gotten into trouble with it.
I also point out that I've been using computers since before most of you were born. In 1969 I went to work for Mohawk Airlines, which was the second airline in the entire world to get a computerized reservations system.
usonian
(23,977 posts)Google is a spy agency. It knows everything you do there (I am sure that they have a shadow profile on me, even though I use them very rarely and don't have an account) they never forget and they gleefully sell your data to advertisers and cops.
I mostly use DuckDuckGo (and others) because they erase any collected data (IP address, browser, OS, etc) daily.
So, when I search "kill switch" I don't get entered in to a database of murder suspects.
Happy and safe computing. ![]()